ePrism SSL VA is the best solution for starting SSL traffic management. To decrypt traffic, the TST based ePrism SSL VA monitors all traffic on all ports transparently allowing it to be connected without modifications to your network.
SOOSAN INT
Security Solutions
SSL Visibility Solution




For standard network devices such as IPS, IDS, SWG and DLP devices, ePrism SSL VA provides visibility into SSL traffic (mostly seen in https) that would otherwise be impossible to analyze. With the rapid growth of SSL traffic, this visibility is more important than ever.
Main function
DPI based SSL Traffic Decryption
Session Transparency Maintenance
Bypass access program Blocking
Key Benefits
Visibility into SSL Traffic
- Provides SSL traffic visibility to block web security threats before they enter your network.
- Prevents malware and ransomware infection.
- Decrypted Traffic Zone can be created to provide decryption for existing security appliances.
Verified Reliability
- Supports a variety of bypass modes to keep the network running smoothly.
- Highly compatible with the existing network environment.
- With installations at over 80 companies, ePrism has proven reliability.
Enterprise Security Enhancement
- Complies with security rules strengthened every year.
- Blocks threats to information assets before infection.
- Reduces the risk of reputation and economic costs from security incidents.
Product Features
High Performance TST based Session Processing
Supports DTZ Deplyments
Highly Compatible with 3rd party Devices
Certificate Installation Distribution and Management
Detailed SSL Traffic Analysis and Log Searching
Various Installation Methods and Options for Ease Use
TST (TCP Session Transparency) based SSL Decryption
- Using the DPI (Deep Packet Inspection) engine, only SSL/TLS sessions are selected for decryption after the connection between the user and the server has been established.
- Supports decryption of non-standard SSL/TLS traffic without degrading network performance.
- Maintains session transparency (5 Tuple: Source IP, Destination IP, Source Port, Destination Port, Protocol).
DTZ (Decrypted Traffic Zone) Deployments
- Enables existing network devices that can’t recognize encrypted traffic to analyze it by providing the devices decrypted traffic.
- Supports Active Port in In-Line configuration and Passive Port in Mirror configuration at the same time.
- Supports bidirectional analysis and blocking of ingress and egress TLS/ SSL traffic.
Support for various configurations
- Supports inline active ports and mirror passive ports simultaneously.
- Support Forward/Reverse form and analyzes and delivery two-way TLS/SSL traffic.
M.P.T(Message Path Through)
- Supports revising blocking messages sent by security devices to match the original session’s RST packet.
- The blocking messages from 3rd party devices are shown as originally intended when https sites are blocked.
- MPT enables users to easily determine which product’s security policy was violated traffic is blocked.
Certificate Distribution and Management
- Supports redirection for certificate downloads and includes a status monitoring page for the convenience of admins.
- Includes a management page for the certificate installation/distribution/status on local devices.
- Provides a certificate installer for various OSs (Windows, Mac OS, iOS, Android, and etc.).
Anonymizer Blocking
- Capable of blocking several anonymization patters through analysis of encrypted and plaintext traffic.
- Regular updates to the protocol database ensure the latest protocols are known.
Provides SSL traffic visibility
Proven Reliability
- Proactively block web threats by ensuring you have visibility into SSL traffic.
- Prevent malware and ransomware infections.
- Create SSL decryption zones to provide standard security appliances decrypted traffic.
Prevent Distribution of Internal Data
- Analyzes and blocks anonymizers.
- Prevent infection via malware or ransomware.
- Provides L7 traffic classification (including anonymizing protocols).
- Periodic protocol database updates are included.
Proven Reliability
- Provides optimal compatibility with your network environment.
- Supports network reliability with a variety of bypass options.
- Tested stability in public, financial, and corporate environments.
- Production verified with approximately 80 references.
Raise the Level of Your IT Security
- Allows for identification and prevention of potential threats to your assets.
- Improve your corporate image and customer loyalty by building a compete security solution.
- Aids in rising to the level of constantly increasing information security regulations.
- In the event of a security incident, can help reduce economic and reputational costs.
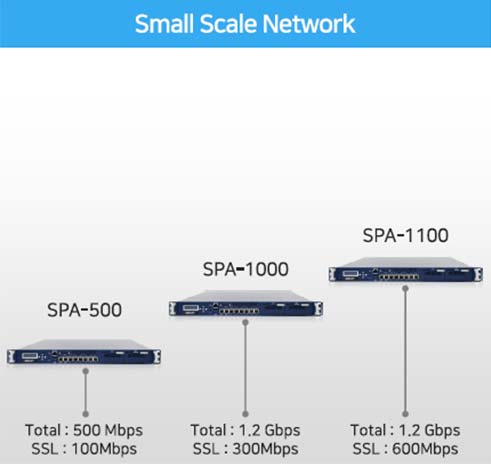
Product Line Up